One of many largest sources of confusion within the query of blockchain safety is the exact impact of the block time. If one blockchain has a block time of 10 minutes, and the opposite has an estimated block time of 17 seconds, then what precisely does that imply? What’s the equal of six confirmations on the 10-minute blockchain on the 17-second blockchain? Is blockchain safety merely a matter of time, is it a matter of blocks, or a mix of each? What safety properties do extra complicated schemes have?
Notice: this text is not going to go into depth on the centralization dangers related to quick block occasions; centralization dangers are a significant concern, and are the first motive to not push block occasions all the way in which all the way down to 1 second regardless of the advantages, and are mentioned at way more size on this earlier article; the aim of this text is to elucidate why quick block occasions are fascinating in any respect.
The reply the truth is relies upon crucially on the safety mannequin that we’re utilizing; that’s, what are the properties of the attackers that we’re assuming exist? Are they rational, byzantine, economically bounded, computationally bounded, in a position to bribe bizarre customers or not? On the whole, blockchain safety evaluation makes use of certainly one of three totally different safety fashions:
- Regular-case mannequin: there are not any attackers. Both everyone seems to be altruistic, or everyone seems to be rational however acts in an uncoordinated approach.
- Byzantine fault tolerance mannequin: a sure proportion of all miners are attackers, and the remainder are trustworthy altruistic individuals.
- Financial mannequin: there may be an attacker with a finances of $X which the attacker can spend to both buy their very own {hardware} or bribe different customers, who’re rational.
Actuality is a mixture between the three; nonetheless, we will glean many insights by inspecting the three fashions individually and seeing what occurs in every one.
The Regular Case
Allow us to first begin off by trying on the regular case. Right here, there are not any attackers, and all miners merely need to fortunately sing collectively and get alongside whereas they proceed progressively extending the blockchain. Now, the query we need to reply is that this: suppose that somebody despatched a transaction, and okay seconds have elapsed. Then, this individual sends a double-spend transaction attempting to revert their unique transaction (eg. if the unique transaction despatched $50000 to you, the double-spend spends the identical $50000 however directs it into one other account owned by the attacker). What’s the likelihood that the unique transaction, and never the double-spend, will find yourself within the ultimate blockchain?
Notice that, if all miners are genuinely good and altruistic, they won’t settle for any double-spends that come after the unique transaction, and so the likelihood ought to strategy 100% after a number of seconds, no matter block time. One technique to loosen up the mannequin is to imagine a small proportion of attackers; if the block time is extraordinarily lengthy, then the likelihood {that a} transaction will likely be finalized can by no means exceed 1-x, the place x is the share of attackers, earlier than a block will get created. We’ll cowl this within the subsequent part. One other strategy is to loosen up the altruism assumption and as a substitute talk about uncoordinated rationality; on this case, an attacker attempting to double-spend can bribe miners to incorporate their double-spend transaction by inserting a better charge on it (that is basically Peter Todd’s replace-by-fee). Therefore, as soon as the attacker broadcasts their double-spend, will probably be accepted in any newly created block, apart from blocks in chains the place the unique transaction was already included.
We will incorporate this assumption into our query by making it barely extra complicated: what’s the likelihood that the unique transaction has been positioned in a block that may find yourself as a part of the ultimate blockchain? Step one to attending to that state is getting included in a block within the first place. The likelihood that it will happen after okay seconds is fairly properly established:
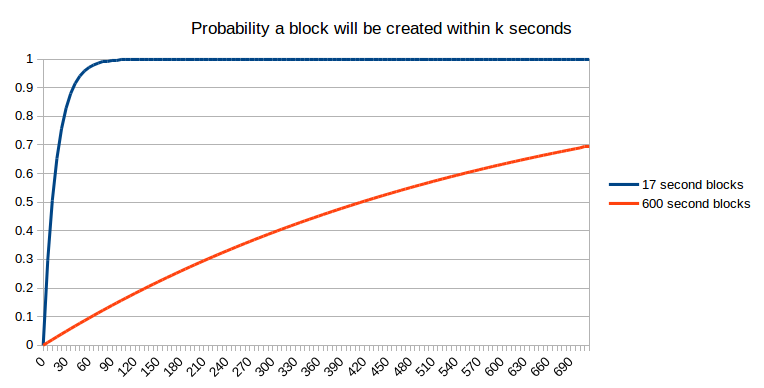
Sadly, entering into one block shouldn’t be the top of the story. Maybe, when that block is created, one other block is created on the identical time (or, extra exactly, inside community latency); at that time, we will assume as a primary approximation that it’s a 50:50 likelihood which of these two blocks the subsequent block will likely be constructed on, and that block will in the end “win” – or, maybe, two blocks will likely be created as soon as once more on the identical time, and the competition will repeat itself. Even after two blocks have been created, it is attainable that some miner has not but seen each blocks, and that miner will get fortunate and created three blocks one after the opposite. The probabilities are seemingly mathematically intractable, so we are going to simply take the lazy shortcut and simulate them:
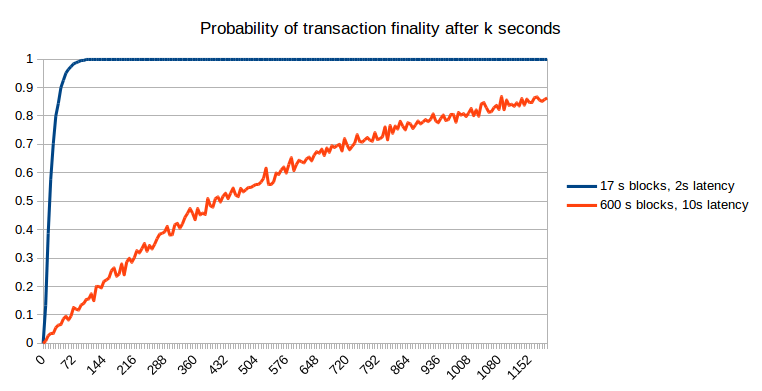
Script right here
The outcomes will be understood mathematically. At 17 seconds (ie. 100% of the block time), the sooner blockchain provides a likelihood of ~0.56: barely smaller than the matheatically predicted 1-1/e ~= 0.632 due to the potential of two blocks being created on the identical time and one being discarded; at 600 seconds, the slower blockchain provides a likelihood of 0.629, solely barely smaller than the anticipated 0.632 as a result of with 10-minute blocks the likelihood of two blocks being created on the identical time may be very small. Therefore, we will see that sooner blockchains do have a slight drawback due to the upper affect of community latency, but when we do a good comparability (ie. ready a specific variety of seconds), the likelihood of non-reversion of the unique transaction on the sooner blockchain is far larger.
Attackers
Now, let’s add some attackers into the image. Suppose that portion X of the community is taken up by attackers, and the remaining 1-X is made up of both altruistic or egocentric however uncoordinated (barring egocentric mining concerns, as much as X it truly doesn’t matter which) miners. The best mathematical mannequin to make use of to approximate that is the weighted random stroll. We begin off assuming {that a} transaction has been confirmed for okay blocks, and that the attacker, who can be a miner, now tries to begin a fork of the blockchain. From there, we characterize the scenario with a rating of okay, which means that the attacker’s blockchain is okay blocks behind the unique chain, and at each step make the statement that there’s a likelihood of X that the attacker will make the subsequent block, altering the rating to k-1 and a likelihood of 1-X that trustworthy miners mining on the unique chain will make the subsequent block, altering the rating to okay+1. If we get to okay = 0, that signifies that the unique chain and the attacker’s chain have the identical size, and so the attacker wins.
Mathematically, we all know that the likelihood of the attacker successful such a recreation (assuming x < 0.5 as in any other case the attacker can overwhelm the community it doesn’t matter what the blockchain parameters are) is:
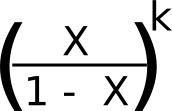
We will mix this with a likelihood estimate for okay (utilizing the Poisson distribution) and get the web likelihood of the attacker successful after a given variety of seconds:
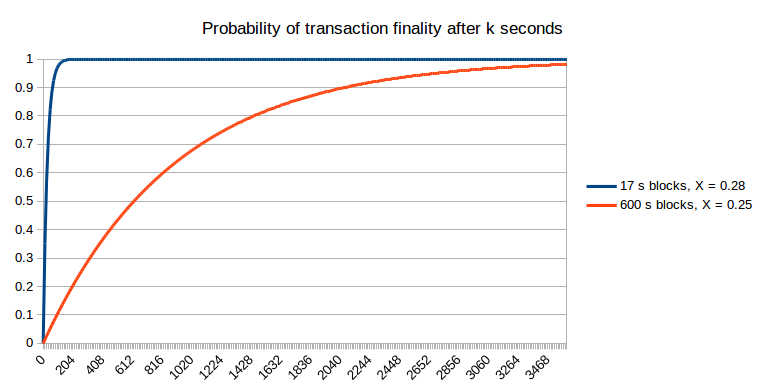
Script right here
Notice that for quick block occasions, we do should make an adjustment as a result of the stale charges are greater, and we do that within the above graph: we set X = 0.25 for the 600s blockchain and X = 0.28 for the 17s blockchain. Therefore, the sooner blockchain does permit the likelihood of non-reversion to achieve 1 a lot sooner. One different argument which may be raised is that the diminished price of attacking a blockchain for a brief period of time over a protracted period of time signifies that assaults in opposition to quick blockchains might occur extra often; nonetheless, this solely barely mitigates quick blockchains’ benefit. For instance, if assaults occur 10x extra typically, then because of this we must be comfy with, for instance, a 99.99% likelihood of non-reversion, if earlier than we had been comfy with a 99.9% likelihood of non-reversion. Nonetheless, the likelihood of non-reversion approaches 1 exponentially, and so solely a small variety of further confirmations (to be exact, round two to 5) on the sooner chain is required to bridge the hole; therefore, the 17-second blockchain will seemingly require ten confirmations (~three minutes) to realize the same diploma of safety underneath this probabilistic mannequin to 6 confirmations (~one hour) on the ten-minute blockchain.
Economically Bounded Attackers
We will additionally strategy the topic of attackers from the opposite facet: the attacker has $X to spend, and may spend it on bribes, near-infinite instantaneous hashpower, or anything. How excessive is the requisite X to revert a transaction after okay seconds? Primarily, this query is equal to “how a lot financial expenditure does it take to revert the variety of blocks that may have been produced on high of a transaction after okay seconds”. From an expected-value standpoint, the reply is straightforward (assuming a block reward of 1 coin per second in each instances):
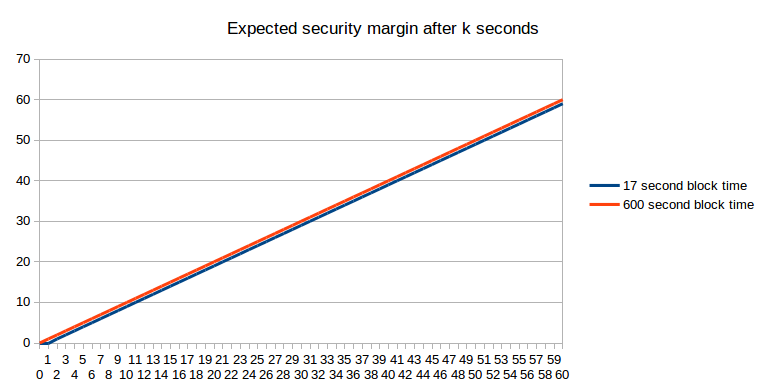
If we consider stale charges, the image truly turns barely in favor of the longer block time:
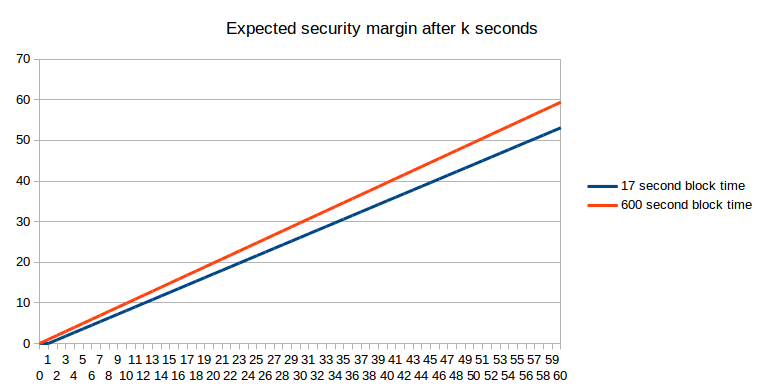
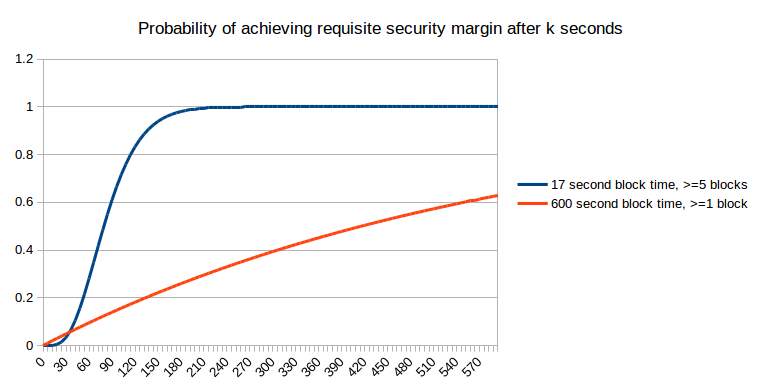
However “what’s the anticipated financial safety margin after okay seconds” (utilizing “anticipated” right here within the formal probability-theoretic sense the place it roughly means “common”) is definitely not the query that most individuals are asking. As an alternative, the issue that considerations bizarre customers is arguably certainly one of them eager to get “sufficient” safety margin, and eager to get there as shortly as attainable. For instance, if I’m utilizing the blockchain to buy a $2 espresso, then a safety margin of $0.03 (the present bitcoin transaction charge, which an attacker would want to outbid in a replace-by-fee mannequin) is clearly not sufficient, however a safety margin of $5 is clearly sufficient (ie. only a few assaults would occur that spend $5 to steal $2 from you), and a safety margin of $50000 shouldn’t be a lot better. Now, allow us to take this strict binary sufficient/not-enough mannequin and apply it to a case the place the cost is so small that one block reward on the sooner blockchain is larger than the fee. The likelihood that we are going to have “sufficient” safety margin after a given variety of seconds is precisely equal to a chart that we already noticed earlier:

Now, allow us to suppose that the specified safety margin is price between 4 and 5 occasions the smaller block reward; right here, on the smaller chain we have to compute the likelihood that after okay seconds no less than 5 blocks could have been produced, which we will do through the Poisson distribution:
Now, allow us to suppose that the specified safety margin is price as a lot because the bigger block reward:
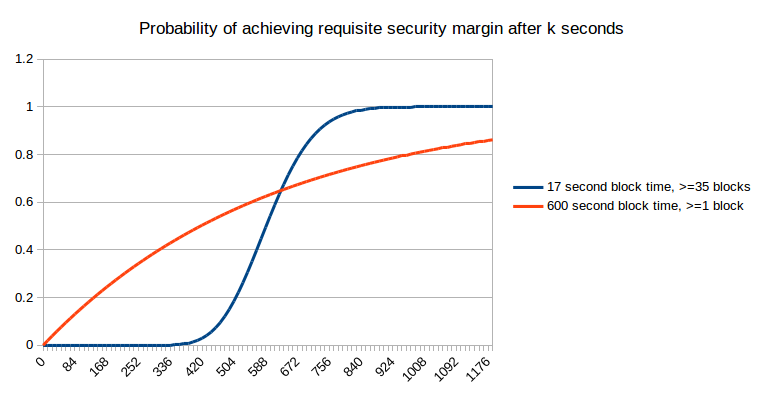
Right here, we will see that quick blocks not present an unambiguous profit; within the brief time period they really harm your possibilities of getting extra safety, although that’s compensated by higher efficiency in the long run. Nonetheless, what they do present is extra predictability; somewhat than a protracted exponential curve of attainable occasions at which you’re going to get sufficient safety, with quick blocks it’s just about sure that you’re going to get what you want inside 7 to 14 minutes. Now, allow us to maintain rising the specified safety margin additional:
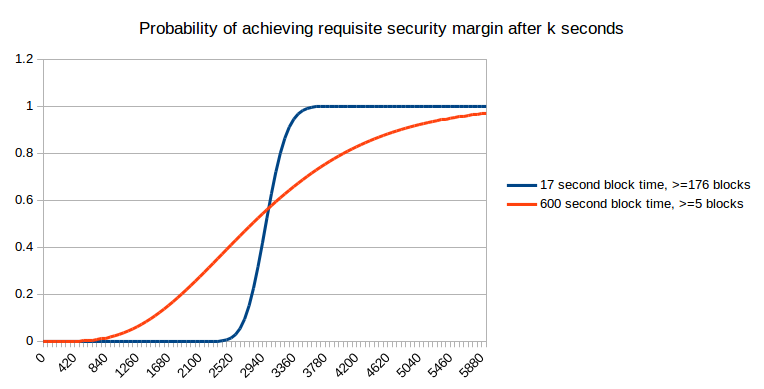
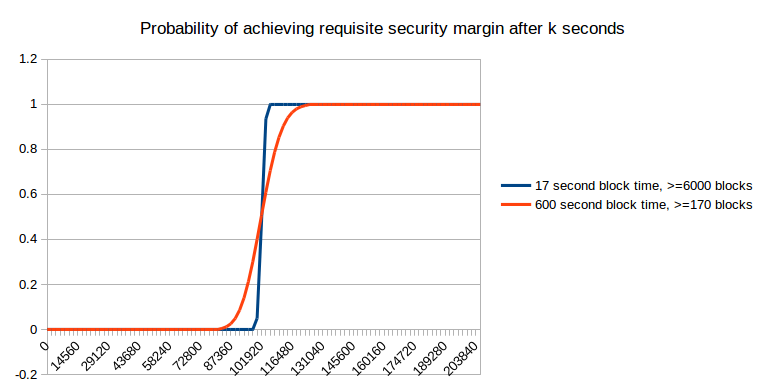
As you possibly can see, as the specified safety margin will get very excessive, it not actually issues that a lot. Nonetheless, at these ranges, it’s important to wait a day for the specified safety margin to be achieved in any case, and that could be a size of time that the majority blockchain customers in apply don’t find yourself ready; therefore, we will conclude that both (i) the financial mannequin of safety shouldn’t be the one that’s dominant, no less than on the margin, or (ii) most transactions are small to medium sized, and so truly do profit from the larger predictability of small block occasions.
We also needs to point out the potential of reverts resulting from unexpected exigencies; for instance, a blockchain fork. Nonetheless, in these instances too, the “six confirmations” utilized by most websites shouldn’t be sufficient, and ready a day is required with a purpose to be really protected.
The conclusion of all that is easy: sooner block occasions are good as a result of they supply extra granularity of data. Within the BFT safety fashions, this granularity ensures that the system can extra shortly converge on the “appropriate” fork over an incorrect fork, and in an financial safety mannequin because of this the system can extra shortly give notification to customers of when a suitable safety margin has been reached.
In fact, sooner block occasions do have their prices; stale charges are maybe the biggest, and it’s after all essential to steadiness the 2 – a steadiness which would require ongoing analysis, and even perhaps novel approaches to fixing centralization issues arising from networking lag. Some builders might have the opinion that the consumer comfort offered by sooner block occasions shouldn’t be definitely worth the dangers to centralization, and the purpose at which this turns into an issue differs for various individuals, and will be pushed nearer towards zero by introducing novel mechanisms. What I’m hoping to disprove right here is solely the declare, repeated by some, that quick block occasions present no profit in any respect as a result of if every block is fifty occasions sooner then every block is fifty occasions much less safe.
Appendix: Eyal and Sirer’s Bitcoin NG
A latest fascinating proposal introduced on the Scaling Bitcoin convention in Montreal is the thought of splitting blocks into two sorts: (i) rare (eg. 10 minute heartbeat) “key blocks” which choose the “chief” that creates the subsequent blocks that comprise transactions, and (ii) frequent (eg. 10 second heartbeat) “microblocks” which comprise transactions:
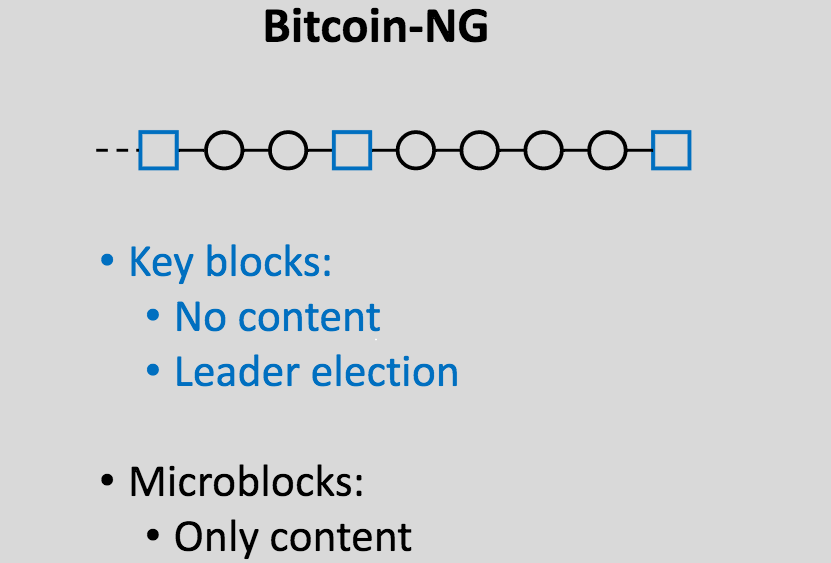
The speculation is that we will get very quick blocks with out the centralization dangers by basically electing a dictator solely as soon as each (on common) ten minutes, for these ten minutes, and permitting the dictator to supply blocks in a short time. A dictator “ought to” produce blocks as soon as each ten seconds, and within the case that the dictator makes an attempt to double-spend their very own blocks and create an extended new set of microblocks, a Slasher-style algorithm is used the place the dictator will be punished in the event that they get caught:
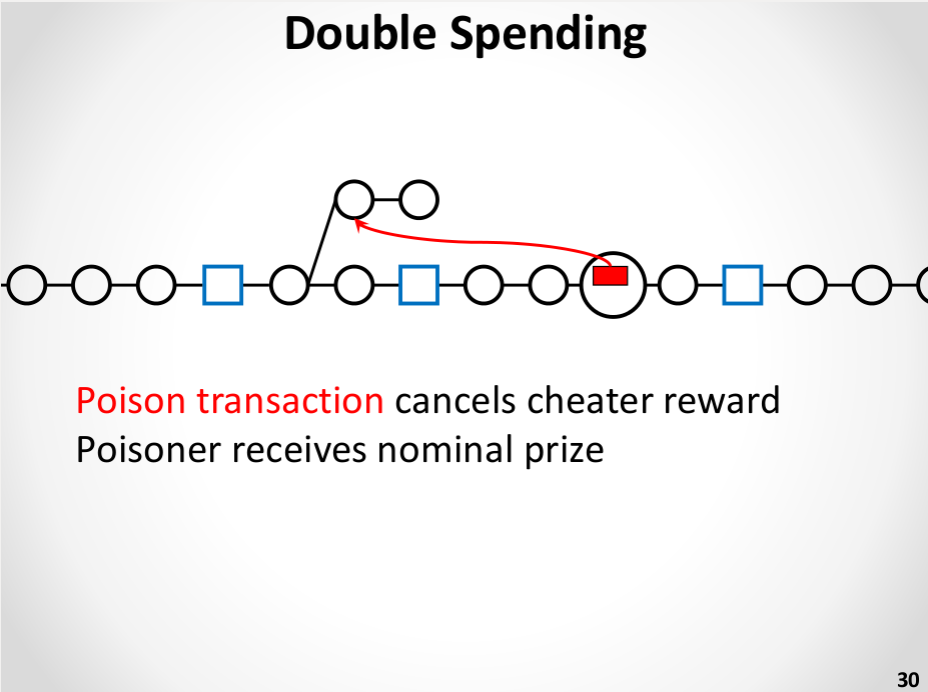
That is definitely an enchancment over plain previous ten-minute blocks. Nonetheless, it’s not practically as efficient as merely having common blocks come as soon as each ten seconds. The reasoning is straightforward. Below the economically-bounded attacker mannequin, it truly does provide the identical chances of assurances because the ten-second mannequin. Below the BFT mannequin, nonetheless, it fails: if an attacker has 10% hashpower then the likelihood {that a} transaction will likely be ultimate can’t exceed 90% till no less than two key blocks are created. In actuality, which will be modeled as a hybrid between the financial and BFT situations, we will say that though 10-second microblocks and 10-second actual blocks have the identical safety margin, within the 10-second microblock case “collusion” is simpler as inside the 10-minute margin just one get together must take part within the assault. One attainable enchancment to the algorithm could also be to have microblock creators rotate throughout every inter-key-block section, taking from the creators of the final 100 key blocks, however taking this strategy to its logical conclusion will seemingly result in reinventing full-on Slasher-style proof of stake, albeit with a proof of labor issuance mannequin connected.
Nonetheless, the final strategy of segregating chief election and transaction processing does have one main profit: it reduces centralization dangers resulting from gradual block propagation (as key block propagation time doesn’t rely upon the scale of the content-carrying block), and thus considerably will increase the utmost protected transaction throughput (even past the margin offered by way of Ethereum-esque uncle mechanisms), and for that reason additional analysis on such schemes ought to definitely be completed.
from Ethereum – My Blog https://ift.tt/LyWc4D3
via IFTTT